What Is an HTTP Proxy? How It Works and When to Use It.
When your browser sends a request to a website, it usually goes straight to the destination server and comes back with a response. An HTTP proxy sits in the middle of that conversation like a skilled receptionist—receiving your request, deciding how best to handle it, and then forwarding it on your behalf. Because it understands the Hypertext Transfer Protocol (HTTP), it can read request and response metadata, apply rules, cache content, and add helpful controls for performance and security.
How an HTTP Proxy Works
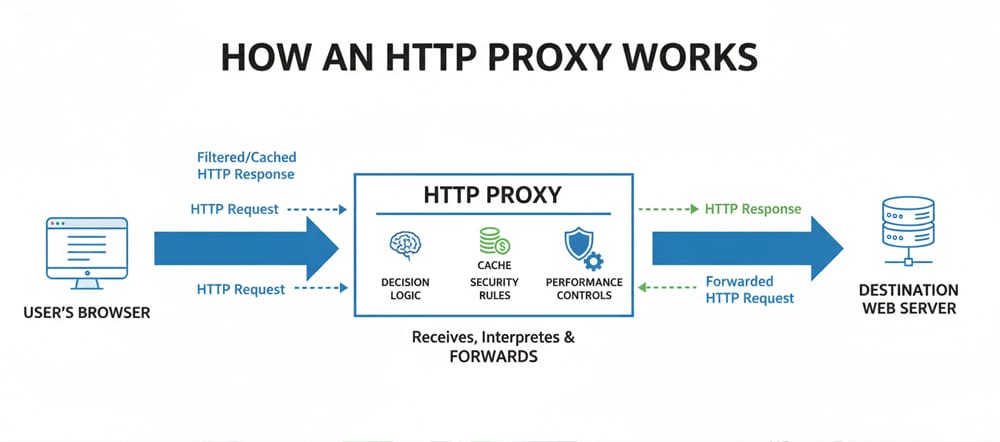
Think of the proxy as a smart relay. Your client connects to the proxy and says, “Please fetch this page.” The proxy opens a new connection to the target server, attaches or adjusts headers (such as User-Agent, Accept-Language, or authentication tokens when configured), and then returns the server’s reply. This indirection means policies and optimizations can be enforced in one place rather than on every device.
Because the proxy speaks HTTP, it can act at the application layer. That’s powerful: it can cache frequently requested pages, compress responses, rewrite headers, and log traffic in a structured way. For organizations, this creates a central point to observe and manage web usage, while for developers it offers a predictable gateway for testing, automation, and integration.
Key Components and Terminology
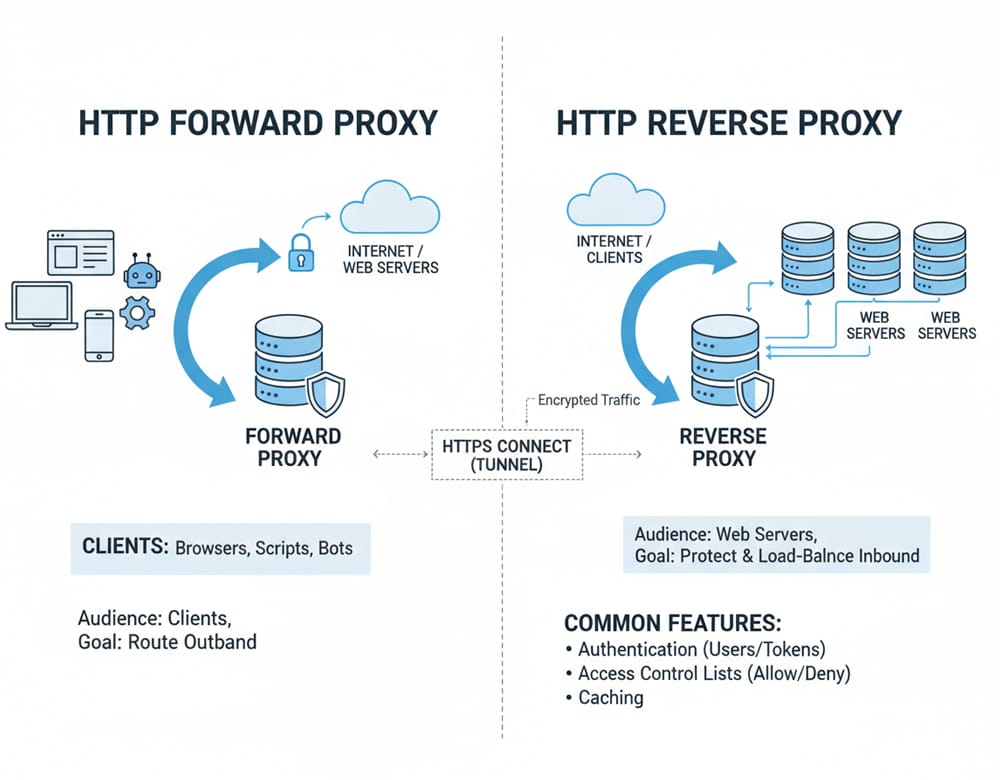
An HTTP forward proxy serves clients—browsers, scripts, bots—routing their outbound web requests. By contrast, a reverse proxy sits in front of web servers, protecting and load-balancing inbound requests. Both use similar mechanics, but their audiences and goals differ.
You’ll also encounter HTTPS via the HTTP CONNECT method, where the proxy establishes a tunnel for encrypted traffic. Even then, the proxy can still enforce connection policies (e.g., which hosts are allowed) without inspecting content. Other common features include authentication (requiring usernames/passwords or tokens), access control lists (allow/deny rules), and caching to speed up repeat fetches and reduce bandwidth.
Common Use Cases and Practical Benefits
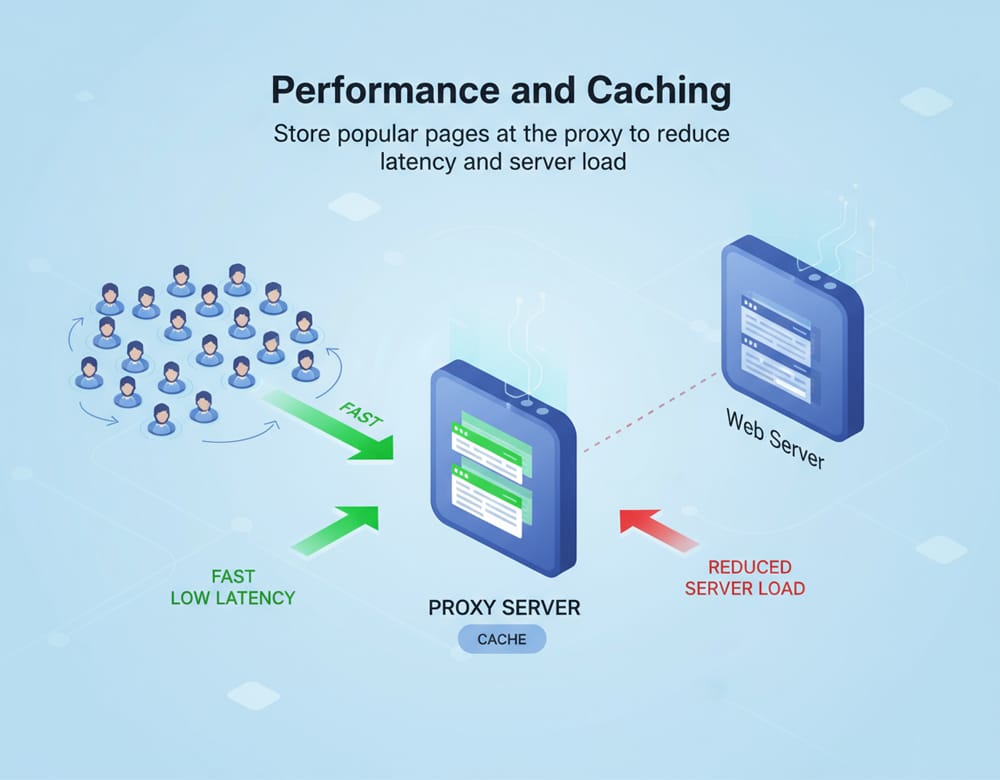
- Performance and caching: Store popular pages at the proxy to reduce latency and server load.
- Traffic governance: Centralize logging and apply usage policies consistently across teams or apps.
- Testing and automation: Route crawlers, QA tools, and CI pipelines through a predictable endpoint.
- Geo-targeted operations: Choose egress locations to validate localized content or prices.
- Security overlays: Enforce allowlists/denylists, sanitize headers, and standardize TLS versions via policy.
A good way to picture it: an HTTP proxy is like a well-staffed switchboard. Calls (requests) are routed efficiently, recorded when needed, and handled according to clear rules so the overall system runs smoother.
HTTP vs. HTTPS vs. SOCKS: Quick Comparison
| Protocol | What It Handles | Typical Ports | Pros | Considerations |
HTTP Proxy | Application-layer HTTP requests and responses | 80, 8080, 3128 | Understands HTTP headers, supports caching, header rules, auth | Best for web traffic; not suited to arbitrary non-HTTP protocols |
| HTTPS via CONNECT | Tunneling encrypted HTTP(S) sessions through the proxy | 443 (tunneled) | Preserves end-to-end encryption; proxy still enforces access rules | Limited visibility into payload; caching typically disabled |
| SOCKS5 (contrast) | Transport-level, protocol-agnostic forwarding | 1080 | Works with many protocols beyond HTTP | Less application-aware; lacks native HTTP header controls |
This quick view highlights why HTTP proxies shine for web-specific workflows: they’re fluent in the language of the web and can apply optimizations that generic tunnels can’t.
How to Choose a Reliable HTTP Proxy Provider
Start with performance: low latency and consistent throughput matter more than peak speeds that only appear in lab conditions. Evaluate IP quality—clean, reputable addresses reduce blocks and friction. Look for fine-grained targeting (country, region, city), session control (rotating vs. sticky), and transparent pricing so you can forecast costs as your usage grows. Don’t overlook support quality either; rapid, expert help is invaluable when a mission-critical workflow needs attention.
If you’re exploring providers, you can learn more about capabilities and setup options here: https://proxys.io/en/p/http-proxy.
Setup Tips, Security, and Best Practices
Configuration usually takes just a few fields: proxy host, port, and—if required—credentials. Browsers allow system-wide or per-profile proxy settings; command-line tools and HTTP client libraries accept proxy URLs (e.g., http://user:pass@host:port). In automation, centralize those settings via environment variables like HTTP_PROXY and HTTPS_PROXY to keep scripts clean and portable.
For resilience, define timeouts and retries thoughtfully—too aggressive and you flood endpoints; too lax and you stall pipelines. Enable connection pooling where possible to reuse sockets. If you employ allowlists/denylists, document them and review periodically to avoid accidental outages. Finally, log just enough to troubleshoot while respecting privacy and compliance requirements. Good proxy hygiene—clear rules, minimal secrets in code, regular credential rotation—turns a basic relay into a dependable, high-leverage part of your stack.